CyberX, the IIoT and industrial control system (ICS) security company, today announced the availability of its 2019 Global ICS & IIoT Risk Report.
The data shows major security gaps remain in key areas such as plain-text passwords, direct connections to the internet, and weak anti-virus protections.
Although the prevalence of Windows XP and other legacy Windows systems has decreased year-over-year — driven top-down by management in the aftermath of NotPetya’s financial damage — CyberX is still finding unpatchable Windows systems in slightly more than half of all industrial sites.
Unlike questionnaire-based surveys, the CyberX report is based on analysing real-world traffic from production ICS networks, making it a more accurate representation of the current state of ICS security.
Now in its second year, the report is based on data captured over the past 12 months from more than 850 production ICS networks across six continents and all industrial sectors including energy and utilities, manufacturing, pharmaceuticals, chemicals, and oil and gas.
According to Andy Bochman, senior grid strategist for national and homeland security at the Idaho National Laboratory (INL) and a nationally recognized cybersecurity expert: “If you are in critical infrastructure you should plan to be targeted. And if you’re targeted, you will be compromised. It’s that simple.”
But that doesn’t mean nothing can be done. Ruthless prioritisation is key.
Many problems exist, but not all of them need to be solved at once.
In the report, CyberX lays out a series of eight steps towards protecting an organisation’s most essential assets and processes. These include: continuous ICS network monitoring to immediately spot attempts to exploit unpatched systems before attackers can do any damage; threat modelling to prioritise mitigation of the highest consequence attack vectors; and more granular network segmentation.

Key Findings
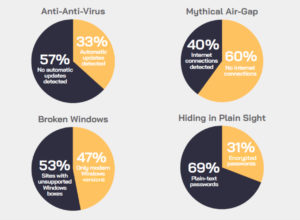
* Hiding in plain sight: 69% of industrial sites have plain text passwords traversing the network. Lack of encryption in legacy protocols like SNMP and FTP exposes sensitive credentials, making cyber-reconnaissance and subsequent compromise relatively easy.
The air-gap — still a myth: 40% of sites have at least one direct connection to the public internet. Whether for convenience or inattention, many industrial networks continue to be connected to the public internet.
With digitisation as a key business driver, operational technology (OT) networks are now also increasingly connected to corporate IT networks, providing additional digital pathways for attackers.
*Anti-anti-virus: 57% are still not running any anti-virus protections that update signatures automatically. Anti-virus programs are still a fundamental defence against malware, but signatures change daily, and the lack of automated updates makes AV programs largely ineffective.
* Broken Windows: 53% of sites have outdated Windows systems like XP. These systems no longer receive security patches from Microsoft, but with NotPetya delivering C-level attention to the issue for the first time, we saw a marked improvement this year — from 3 out of 4 sites with legacy Windows systems in 2017 to 53% in this year’s report.
* Indecent exposure: 16% have at least one Wireless Access Point (WAP). Misconfigured WAPs can be accessed by unauthorised laptops and mobile devices. What’s more, sophisticated malware such as VPNFilter target access points such as routers and VPN gateways, enabling attackers to capture MODBUS traffic, perform network mapping, destroy router firmware, and launch attacks on OT endpoints. This means that routers should also be inventoried and patched to prevent these attacks.
“We’re not here to create FUD, but we think it’s important for business leaders to have a data-driven view of ICS risk so they can ask the right questions,” said Dan Shugrue, senior director of industrial cybersecurity for CyberX. “We’re definitely making progress in reducing ICS risk, but we have a long way to go. Reducing ICS risk is a journey — most of these ICS networks were designed decades ago, long before cybersecurity was a key design priority.”
CyberX delivers a industrial cybersecurity platform built by blue-team military cyber-experts with nation-state expertise defending critical infrastructure.
 Engineer News Network The ultimate online news and information resource for today’s engineer
Engineer News Network The ultimate online news and information resource for today’s engineer