In today’s connected world, with the Industrial Internet of Things and increased adoption of industry 4.0, businesses must deal with more and more connected devices. Security is key to success here and should not be ignored, says Tim Ricketts
Historically there has been a convergence between IT (Information Technology) and OT (Operational Technology).
There is now a real need for data from the plant floor to the top floor business systems. To date, this has been achieved by connecting firewalls to control the traffic flow and allowing production data to be made available for business information needs.
However, if you have a misconfigured firewall, your OT network is at risk from the Internet, as PLCs and automation equipment will be exposed to external infiltration.
Imagine the following scenario. A person is updating a control system; the media is stored on a USB memory device, but the USB memory device has been infected because that person used the device at home the previous evening, which does not have a current active anti-virus.
The payload has now been installed as part of a file transfer and has become ‘active’.
The malware is now distributing itself through the network PCs and is trying to phone home.
Eventually, the malware discovers an open port on the firewall and is able to phone home and deliver a RAT (Remote Access Trojan). This provides a backdoor for remote access by a third party. Before you’re even aware of it, your OT system is infected with a Ransomware demanding £250,000 in bit coins to provide the keys: no real skills were involved here, just human error.
This is just one fairly simple scenario. A more sinister scenario could be that once the payload has been delivered, you’re now under attack in a very stealth way, your control traffic is being decoded, protocols and devices are being discovered as the attackers are now learning your network, devices and control philosophy ready to launch an attack. This can take months of preparation and finally an attack is launched to disrupt the operation, modify recipes of pharmaceutical batches for blackmail exploitation, turn off the lights or stop the production.
During this process, PLC code (data words in data blocks) may have been modified, all under the radar.
MAC Solutions has looked at a couple of OT Cyber attack scenarios. You may be asking yourself what can we do as a business to help mitigate these real threats. MAC Solutions has been working in OT since its inception in 1996 and is a technology vendor and trusted advisor to many European and UK companies. Over the past few years our clients have recognised that they can no longer say that their systems are protected because they are ‘air gapped’ and therefore are immune to cyber attacks.If the above security threats are broken down, we can begin to see which solutions can be provided by MAC Solutions:
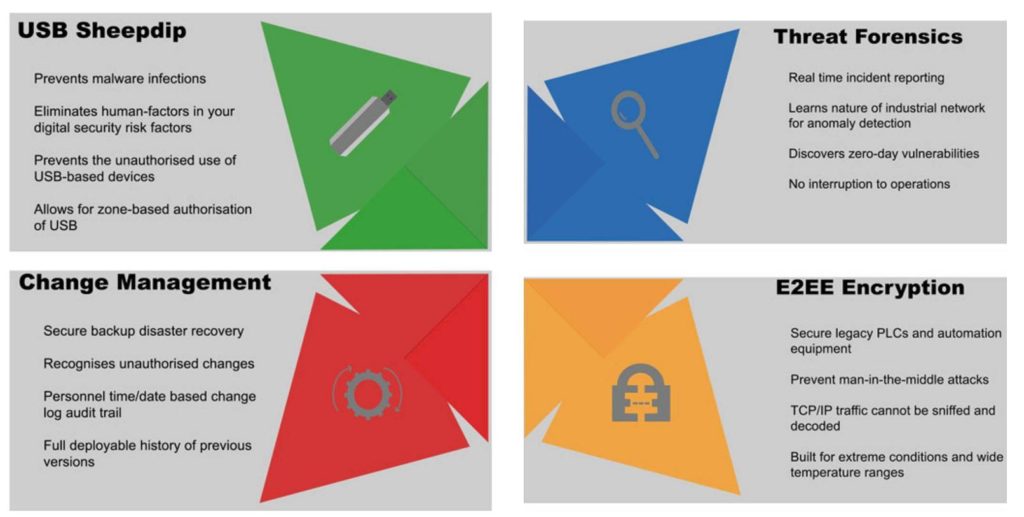
* USB memory devices can be controlled by preventing the endpoint computer accepting a device unless it has been scanned and verified first.
* PLC code changes can be protected by daily comparisons and by reporting on any unauthorised changes.
* Traffic scanning and ingress protection can be identified by Intrusion Detection Systems that are specifically designed for OT network traffic.
* Inter-communications between endpoint devices can be encrypted at wire speed to prevent control traffic being interpreted and a ‘Man in the Middle’ attack launched.
* Firewalls to be replaced with unidirectional gateways, so data can be mirrored between OT and IT, traffic only flows in one direction at the speed of light using data diode technology.
Tim Ricketts is Director of MAC Solutions.
 Engineer News Network The ultimate online news and information resource for today’s engineer
Engineer News Network The ultimate online news and information resource for today’s engineer